Google Ads is a powerful advertising platform with strict policies to protect users from malicious or unwanted software. If your ad is disapproved for this reason, it means that Google has detected that your website or landing page contains malware, spyware, or other types of unwanted software.
Here are some steps you can take to resolve this issue and get your ad approved again:
We encounter cases where, after recovering and securing a WordPress website, Google Ads still disapproves the website, citing “malicious or unwanted software.” Even after contacting Google Ads support, their response remains the same. Below are two sample links that illustrate this issue.
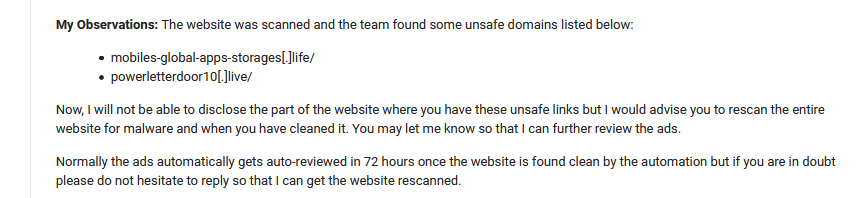
The website was scanned and the team found some unsafe domains listed below:
mobiles-global-apps-storages[.]life/
powerletterdoor10[.]live/Now, I cannot disclose the part of the website where you have these unsafe links, but I would advise you to rescan the entire website for malware when you have cleaned it. You may let me know so that I can further review the ads.
Follow these steps to identify if those malicious links exist and how to resolve them and get google ads approved again.
If you’ve hired the Securewp.net team to recover and secure your WordPress website and are facing Google ads disapproval issues, please don’t hesitate to reach out to us via support ticket or live chat. We guarantee to have this resolved for you within seven business days.
Step 1: Get Links from the Support
First of all, contact Google Ads support, ask for details, ask for what they got on the website.
You may get a reply within two business days. That reply email will contain links that Google Ads found on your website.
Step 2: Find the hidden links.
First, try Securewp.net online security scanner to discover hidden links. You will most likely get those links under “external links” if the website is actively infected and those links exist.
If you get nothing suspicious, proceed to these manual steps to be 100% sure.
Check your website’s HTML source code in any web browser like Mozilla Firefox or Chrome.
- 1: Search your website in Google search (Don’t type URL in browser address bar directly)
- 2: Click on any link from the google search result
- 3: Once you get your website fully loaded on your web browser, press.”
CTRL+U” on the keyboard or right-click on your mouse and select “View page source.” - 4: Press “
CTRL+F” to find the string on the HTML source; type the keywords you got from ads supports email, for example: “mobiles-global-apps-storages“, “apu” or “zoneid” in the search box.
Search keyword links can be different for your website. Get your links from the Google Ads support email.
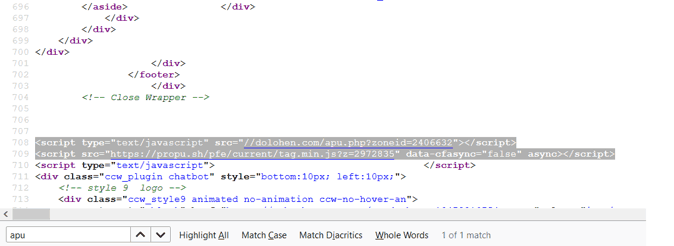
If you can’t locate those links provided by Google Ads support email in your website source code, repeat this finding step in a different browser using another network or VPN.
Tried your best, and still nothing? Please skip to Step 5: Resubmit Ads
If you can identify malicious links in your website’s HTML source code, follow the next step to locate the source of those links and clean them.
Step 3: Check the website database
If those malicious links are hidden in the database, you may locate them by simply searching by domain names or unique keywords.
In our example, we used dolohen, a search term.
Login into PHPMyAdmin >> Select appropriate database name >> click on search
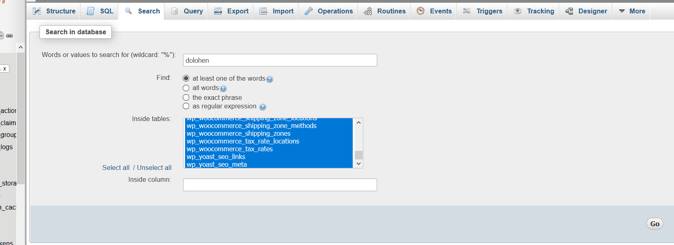
Make sure that you have selected all database tables to search.
If those links exist in the database, you will see several matches like this.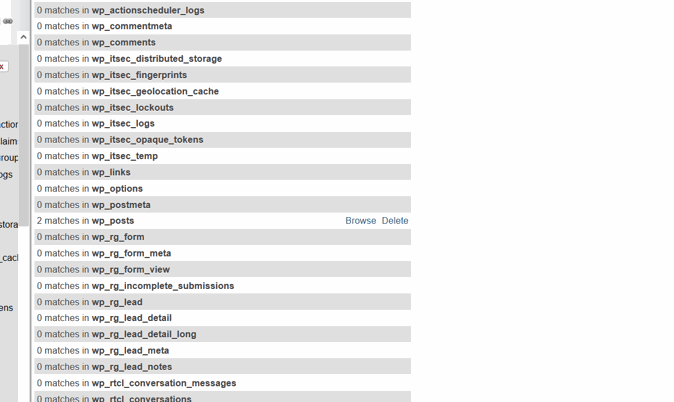
Click on “browse.”
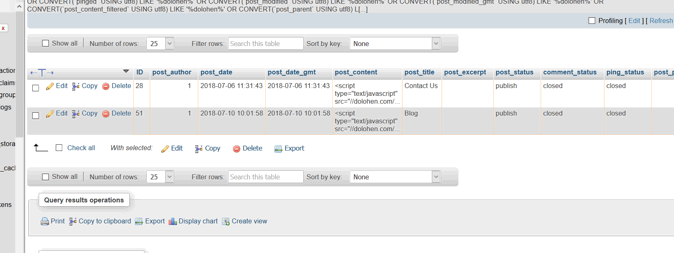
You got your culprit hidden malicious links!
Try different unique search keywords if the result returns nothing.
Step 4: Check website files
In most cases, WordPress security plugins or any other malware scanner can’t identify those malicious javascript links.
As we know, those links are already from Google Ads support email. We will use the SSH terminal to grep search keywords using this command.
grep -Hrn 'dolohen' /var/www/html/wp-content![]()
Once you get the source of those JavaScript links injections, clean it.
Verify again if those malicious JavaScript links still exist in the website HTML source by following Step 1: Check site source code
Step 5: Resubmit Ads
Once you get everything clean, resubmit your ads to Google by editing existing ads.
If you make any simple edit in existing ads, like changing a word, the ad’s status will change to “Under Review.”
- Select the ads you want to resubmit for review.
- In the menu at the top, click Edit.
- Make any changes. You can change a word.
- Click Submit.
Wait and see if the ads get approved, or if you get disapproved email again.
Once your Google Ads are disapproved due to malicious links or unwanted software, there is a high likelihood that they won’t be approved again without a special review from Google Ads Support. To raise the issue to Ads Support, you must provide detailed information on the steps taken to make the website secure and free of malicious content, which may require the assistance of a professional web security expert. Without the expertise of a web security professional, your efforts may not be sufficient to meet Google Ads Support’s standards.
Once your security expert has confirmed that the website is secure and free from malicious activity, proceed to the next step of a particular review request.
Step 6: Contact Google
I assume you have already contacted Google Ads support, and they have sent you some malicious links they found on your website. To ensure your website is clean and secure, you should enlist the help of a web security expert to provide a list of actions to take.
In your reply to the Google Ads support email, let them know you have hired security professionals to clean and secure your website. Provide the document or list of actions taken by your web security expert, and mention that the security professionals could not locate the malicious links after taking those actions. Unfortunately, Google Ads is still detecting the links on your website.
Google Ads support will raise a ticket for you and arrange a review. Within 2-3 business days, you should receive an update from Ads support. If your website is clean, you should receive good news this time! 🙂
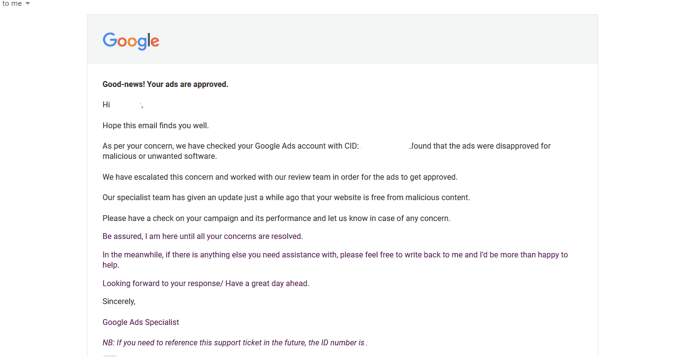
Sample of hidden links we found
You can identify malicious links from HTML source code. Here are some samples we found in different cases we worked on in the past.
We guarantee that your website will be clean, secure, and Google Ads compliant, so you can rest assured that your website will be approved quickly. When submitting an order, mention that Google Ads approval is required to ensure speedy approval. With our assistance, you can know that your website will be approved quickly.